Border line solutions
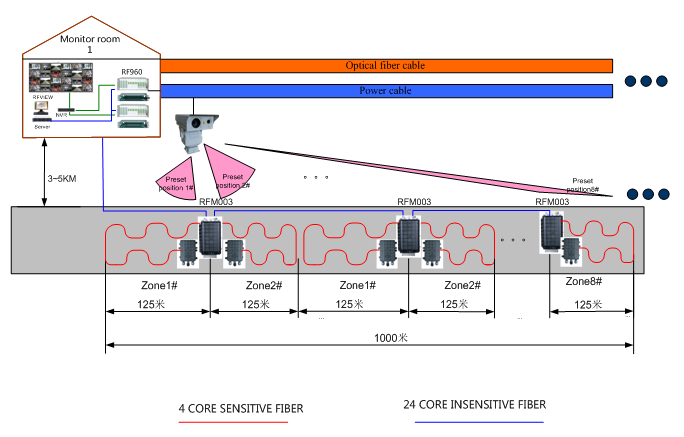
There is no barbed wire fence along the border line, so we use the buried laying scheme to detect the intrusion of people and vehicles. The buried depth is 30cm, one detection host per kilometer, eight defense zones are divided within each kilometer, and eight preset positions of eight defense zone linkage cameras. If an illegal person tries to invade a defense zone, the vibration optical cable laid underground can immediately sense the invasion signal. The equipment generates alarm signals, which can drive the acousto-optic alarm equipment to realize one button alarm. The network management system will alert on the map and call the corresponding preset camera to recheck. The whole system is required to be able to prevent the illegal invasion of the outside world 24 hours.
According to the site conditions, every 1km is taken as a protection unit in the perimeter, and each camp monitors two units. Each 1km is divided into eight defense areas, each of which is about 125m long. One camp is equipped with two intrusion detection devices. The intrusion detection host is placed in the camp monitoring room. All outdoor devices do not need power supply. Two intrusion detection hosts output switching values to NVR to complete video linkage. Rfview is used to manage the linkage. When there is an intrusion, the network management software reports the alarm of the defense area on the map and calls the associated camera screen. The perimeter topology is as follows:
Perimeter topology

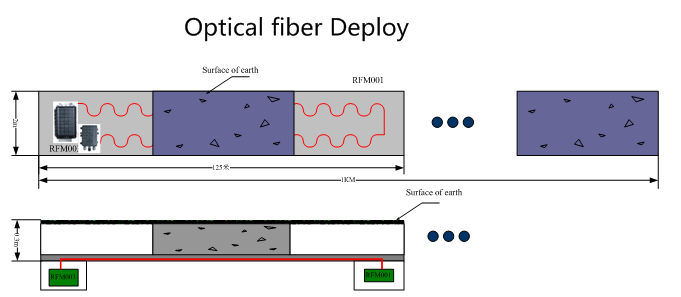
Connection diagram of defense area per kilometer
According to the field situation, the sensor optical cable is buried in the ground with a depth of 30cm and hyperbolic laying. This kind of laying method can detect people, vehicles and other illegal invasion ways. This method is suitable for places with higher alert level. The head and tail of the optical cable shall be reserved with a margin of 3-5M for later maintenance.
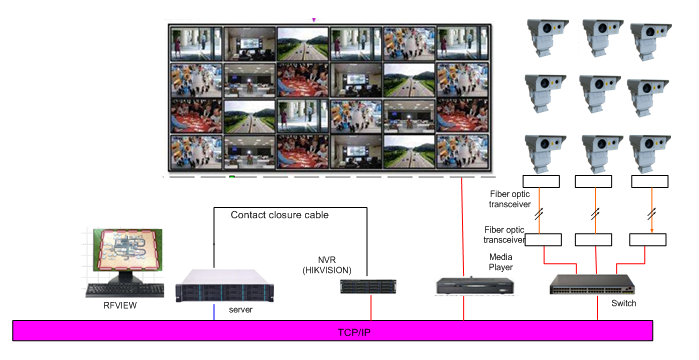
When a perimeter protection system has more defense areas, or there are video monitoring devices (such as cameras, DVR / NVR) in the system, it is necessary to consider how to integrate the system and other types of perimeter protection systems into a whole.
Connect the rf960 switch output to DVR / NVR to realize the linkage with the camera. The linkage mentioned here can be to switch the relevant video picture of the intrusion event to the prominent position, or to drive the PTZ camera to the appropriate preset position immediately after the event to observe the event scene.
Illegal intrusion detection, as shown in the following figure:

Video linkage diagram of camp monitoring center is as follows:
RFVIEW software management

- Support up to 256 zones
- Graphic alarm display of defense area
- Algorithm parameter configuration
- Alarm history
- Privilege classification
- Supports server and client installation versions
-
The server version can configure devices and view alarms
-
The client version can only view configuration and alarms
- Support other switch input alarms
- Support video linkage and embed video pop-up interface

